5-Second Shield
What is the 5-Second Shield
The 5-Second Shield is an intelligent human-machine verification protection system provided by LightCDN, designed to counter malicious requests from automated tools (such as crawlers, CC attack tools, etc.). When suspicious access is detected, it triggers a 5-second waiting page to verify whether the visitor is a real user, effectively intercepting machine traffic and protecting website resources from malicious consumption.
Core Features
| Setting You See | Actual Function |
|---|---|
| QPS Limit | Maximum number of requests per person per second |
| IP Whitelist Mechanism | Verified IPs are automatically added to a temporary whitelist, bypassing subsequent verification |
| Protection Scope | VIP channels (these pages are not checked) |
Applicable Scenarios
● Defending against CC attacks: Intercept malicious high-frequency requests to prevent server overload.
● Anti-crawling: Prevent automated tools from scraping content and protect data security.
● Preventing ticket/order fraud: Limit non-human operations to ensure business fairness.
Configuration Suggestions
● Initial Mode: It is recommended to first enable "Observation Mode," record suspected attack behaviors, and then activate active protection.
● Threshold Adjustment: Adjust the trigger frequency based on business traffic (e.g., triggering when requests exceed 10 times per second).
Frequently Asked Questions
●Q: Does the 5-Second Shield affect SEO?
No. Mainstream search engine crawlers are already allowed.
●Q: Can attackers bypass the 5-Second Shield?
→ The 5-Second Shield combines technologies such as browser fingerprinting and behavioral analysis, making it difficult for automated tools to simulate real user behavior.
Differences Between the 5-Second Shield and CC Defense
The 5-Second Shield uses a 5-second human-machine verification (e.g., JS challenge) to filter low-frequency automated tools (crawlers/ticket fraud), making it suitable for defending against scenarios requiring interactive identification, with minimal disruption to user experience. CC defense directly blocks high-frequency HTTP attacks (e.g., DDoS) based on QPS thresholds and IP characteristics, making it suitable for handling high-intensity flood requests but with a higher risk of false positives. The two can be used together—the 5-Second Shield handles slow attacks, while CC defense deals with violent traffic, forming a layered protection system.
Key Differences Summary
| Comparison Dimension | 5-Second Shield | CC Defense |
|---|---|---|
| Protection Strength | Medium (relies on interactive verification) | High (direct interception) |
| User Experience | Requires a 5-second wait (only on first access) | Completely seamless |
| False Positive Risk | Low (can be restored through verification) | High (may mistakenly block legitimate high-concurrency IPs) |
| Applicable Attacks | Low-frequency automated tools | High-frequency CC/DDoS attacks |
| Configuration Complexity | Simple (only requires setting QPS thresholds) | Complex (requires tuning frequency/rules) |
How to Use the 5-Second Shield in LightCDN
You can go to Security Protection → 5-Second Shield to enable the protection settings.
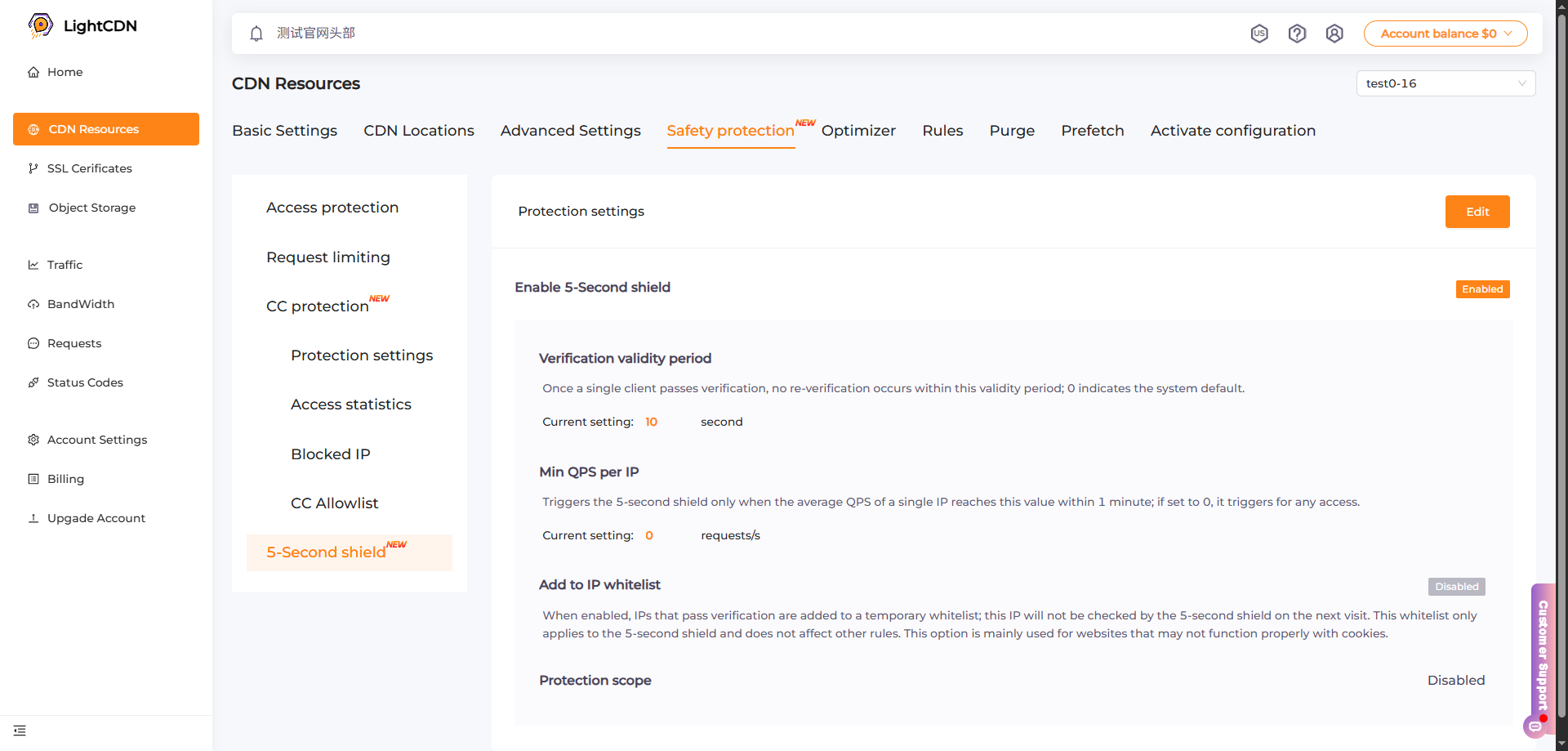 If you are unsure about the function settings, you can leave them unchanged. Adjust and test after understanding the normal traffic volume of your website.
If you are unsure about the function settings, you can leave them unchanged. Adjust and test after understanding the normal traffic volume of your website.